
FEATURE — Another form of computer virus has been showing up on computers everywhere, from hospitals to school districts, law enforcement agencies to homes, and it has the potential to devastate your data. It’s called ransomware and it’s everything the name says: it holds your data hostage until you pay. The rate of infection is high.
“It’s probably increasing,” Darren Jackson of New Age Computers in St. George said. “The hackers are copycatting, so that now there’s more variations of these types of infections.”
Infections are spread via infected websites, infected national servers and social engineering emails.
“Infecting … agencies has been going on for a long time,” Jackson said, “because they don’t take security seriously.”
Another way of infection is through emails purporting to offer you an invoice, a check, a new Facebook friend that you’ve never heard of and other social engineering methods.
“The past few weeks we’ve had a bunch of our business customers having their employees getting emails from themselves labeled ‘Document’ claiming there was an attached scan file,” Jackson said recently. “I just ask them, ‘Did you send a file to yourself? Then why would you expect an email from yourself?‘”
Of course the attachment is not really a scan or an invoice, Jackson said, but an infection that will place the malware on your computer immediately and possibly infect your entire network as well.
Attacks increasing, says FBI
While ransomware has been around for several years, the incidence of attacks rose sharply in 2015, according to the FBI.
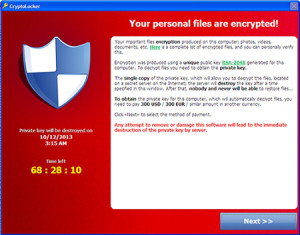
“In a ransomware attack, victims — upon seeing an e-mail addressed to them — will open it and may click on an attachment that appears legitimate, like an invoice or an electronic fax, but which actually contains the malicious ransomware code,” the FBI warning states. “Or the e-mail might contain a legitimate-looking URL, but when a victim clicks on it, they are directed to a website that infects their computer with malicious software.”
The FBI says that social engineering techniques and seeding legitimate websites with malicious code has also been reported.
“Once the infection is present, the malware begins encrypting files and folders on local drives, any attached drives, backup drives, and potentially other computers on the same network that the victim computer is attached to. Users and organizations are generally not aware they have been infected until they can no longer access their data or until they begin to see computer messages advising them of the attack and demands for a ransom payment in exchange for a decryption key. These messages include instructions on how to pay the ransom, usually with bitcoins because of the anonymity this virtual currency provides.”
High profile hospitals and health care providers have been hit with ransomware recently. Hollywood Presbyterian Hospital in Los Angeles, MedStar Health in Washington, D.C., and Methodist Hospital in Henderson, Kentucky, were hit hard this year, forcing doctors and executives to rely on telephones and fax machines to conduct business and relay patient information.
The industry publication “CIO” reported that the two hospitals each paid $17,000 to get their data back after being unable to access any data on their systems for 10 days.
Data backups are key to being able to recover data quickly and without paying a ransom but very few hospitals and doctor’s offices, let alone home users, back up their data at all.
Fighting back
There may be a bright side. Security experts say they have been searching the types of ransomware that is being distributed and are coming up with ways to disable it and decrypt data without a ransom being paid.
Jackson said the FBI recently raided several purveyors of ransomware and have recovered several security keys used to encrypt data.
The computer security company Trend Micro has a large article on their website regarding ransomware, with descriptions of 47 different types of ransomware that are currently known to be circulating. While Trend Micro sells solutions for viruses, ransomware and malware on its site, there are several tools available at no charge the company states will help you recover from an attack and inoculate your computer against future attacks.
Stop the attacks before they start
The easiest way to recover from an attack is to thwart the attacks before they hit your computer. Trend Micro recommends the following to help prevent infections:
- Backup your files regularly
- Apply software patches as soon as they become available. Some ransomware arrives via vulnerability exploits
- Bookmark trusted websites and access these websites via bookmarks
- Download email attachments only from trusted sources
- Scan your system regularly with anti-malware
Resources
Email: [email protected]
Twitter: @STGnews | @NewsWayman
Copyright St. George News, SaintGeorgeUtah.com LLC, 2016, all rights reserved.